What Is Google Dorking and How Hackers Use It to Hack Websites

Google is the encyclopedia of the world-wide-web that carries the answer to all your queries and curiosity. Immediately after all, it is just a world-wide-web index to uncover images, content, and movies, suitable?
Well, if you think so, you are turning a blind eye to the untapped prospective of the behemoth search engine’s crawling abilities. This aspect of Google is lesser-acknowledged to the typical user but propelled successfully by terrible actors to hijack websites and steal delicate data from providers.
Right here, we’ll handle how protection pros and hackers use Google as an efficient reconnaissance instrument to access sensitive details, hijack web sites, and far more.
What Is Google Dorking?
Google dorking or Google hacking is the procedure of feeding state-of-the-art research queries into the Google search motor to hunt for delicate info this kind of as username, password, log files, and so on., of web-sites that Google is indexing because of to internet site misconfiguration. This information is publicly obvious and, in some conditions, downloadable.
A common Google search consists of a seed search term, sentence, or problem. But, in Google dorking, an attacker works by using special operators to increase look for and dictate the website crawler to snipe for extremely specific data files or directories on the world wide web. In most scenarios, they are log files or web page misconfigurations.
How Hackers Use Google Dorking to Hack Sites
Google dorking entails applying exclusive parameters and search operators identified as “dorks” to slim down look for effects and hunt for uncovered delicate facts and security loopholes in websites.
The parameters and operators direct the crawler to glance for unique file styles in any specified URL. The search final results of the query incorporate but are not confined to:
- Open FTP servers.
- A firm’s interior documents.
- Accessible IP cameras.
- Government paperwork.
- Server log files that contains passwords and other delicate data that can be leveraged to infiltrate or disrupt an corporation.
Most-Utilized Google Dorking Operators
Whilst there are tons of operators and parameters that one can apply to a look for query, it only normally takes a handful of them to serve the wants of a security qualified. Listed here are a few commonly used queries:
- inurl: Dictates the crawler to search for URLs that incorporate a specified search phrase.
- allintext: This parameter queries for consumer-specified text in a webpage.
- filetype: This parameter tells the crawler to search for and exhibit a precise file form.
- intitle: Scrapes for web-sites made up of specified key terms in the title.
- site: Lists all the indexed URLs for the specified website.
- cache: When paired with the web site parameter, this 1 displays the cached or older model of a internet site.
- Pipe operator (|): This rational operator will listing benefits that contain possibly of two specified search phrases.
- Wildcard operator (*): This is a wildcard operator that searches for pages that have something related to your look for term.
- Subtract operator (-): This gets rid of unwelcome final results from your lookup.
Is Google Dorking Unlawful?
Though it may perhaps feel intimidating, Google dorking will not land you at the rear of bars, provided you are only working with it to refine your search final results and not infiltrate an group.
It is a vital evil and, in actuality, an encouraged apply amongst electric power end users. Keep in mind that Google is monitoring your queries all the time, so if you access sensitive info or research with destructive intent, Google will flag you as a risk actor.
In situation you are carrying out a pen take a look at or hunting for bug bounty, make sure that you are fully authorized and backed by the corporation. In any other case, if you get caught, matters can get a flip for the worst, and a person can even slap you with a lawsuit.
How to Safeguard Your Web page From Google Hacking
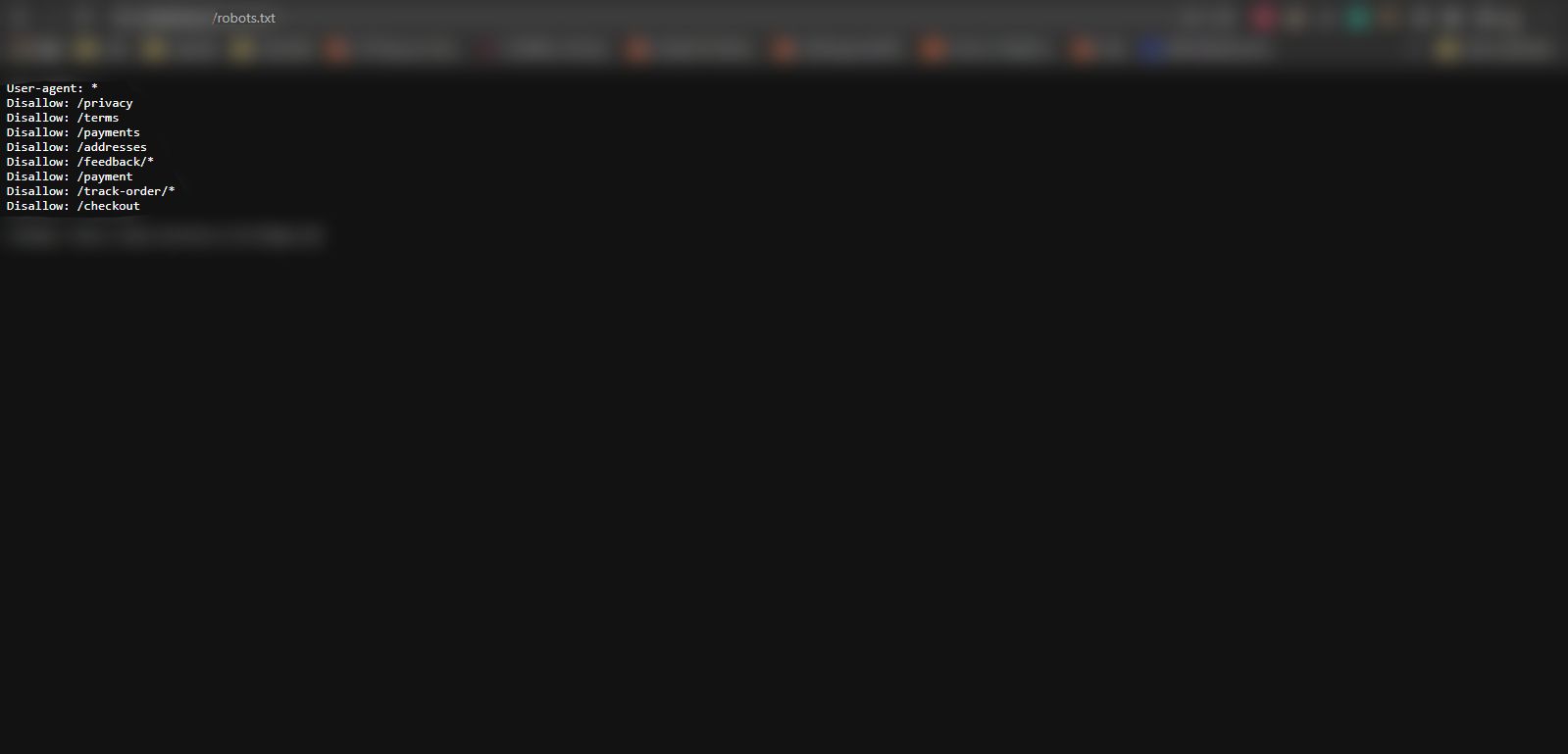
As a webmaster, you have to set up particular defensive countermeasures to tackle Google Dorking. A incredibly easy strategy would be to increase a robots.txt file and disallow access to all sensitive directories. This will keep look for motor crawlers from indexing sensitive information, directories, and URLs as you list them.
Incorporating a robots.txt file to the root directory is a basic great exercise and crucial for the general security of your website. Understand more about why website safety is crucial.
Other methods to mitigate this risk would be to encrypt delicate details such as usernames, passwords, payment details, and so forth., and use Google Lookup Console to clear away pages from search outcomes.
Develop into a Google Power Consumer With Google Dorking
Whilst most of us use Google each day, we rarely at any time get gain of its legitimate prospective. You can harness the usually-disregarded ability of Google dorking ethically to refine your Google-fu and discover just about nearly anything on the world-wide-web.
With the right parameters and key terms in position, the response to all your curiosities and issues will lie at your fingertips, just one particular keypress absent. Find out far more about the finest suggestions and tips to make the most of your Google research.