Log4Shell: How to detect the Log4j vulnerability in your applications
Yesterday the Apache Foundation unveiled an unexpected emergency update for a significant zero-working day vulnerability in Log4j, a ubiquitous logging instrument provided in just about each Java application. The difficulty has been named Log4Shell and acquired the identifier CVE-2021-44228.
The challenge revolves around a bug in the Log4j library that can allow for an attacker to execute arbitrary code on a program that is making use of Log4j to write out log messages. This protection vulnerability has a wide impact and is a little something anyone with an application that contains Log4j wants to quickly fork out focus to.
Why addressing Log4Shell is a main problem
Log4j is a library that is used by numerous Java purposes. It’s a single of the most pervasive Java libraries to date. Most Java purposes log facts, and there’s nothing that tends to make this less complicated than Log4j.
The problem below is getting Log4j for the reason that of the way Java packaging operates. It’s feasible you have Log4j hiding someplace in your application and really do not even know it.
In the Java ecosystem, dependencies are dispersed as Java archive (JAR) files, which are deals that can be used as a Java library. Usually used tools, this kind of as Maven and Gradle, can automatically increase JAR files as you establish your Java application. It’s also feasible for a JAR to consist of another JAR to fulfill a dependency, which implies a vulnerability can be hidden a number of amounts down in your application. In some situations, a single dependency pulls in hundreds of other dependencies making it even much more challenging to come across.
Fundamentally, in the Java planet, you can have a JAR nested in a JAR nested in a JAR. This makes numerous levels that all require to be investigated. Just wanting at the JARs your undertaking pulls in instantly may well not be adequate, since Log4j could be hiding inside of of another JAR file!
Scan for Log4j with open resource tools
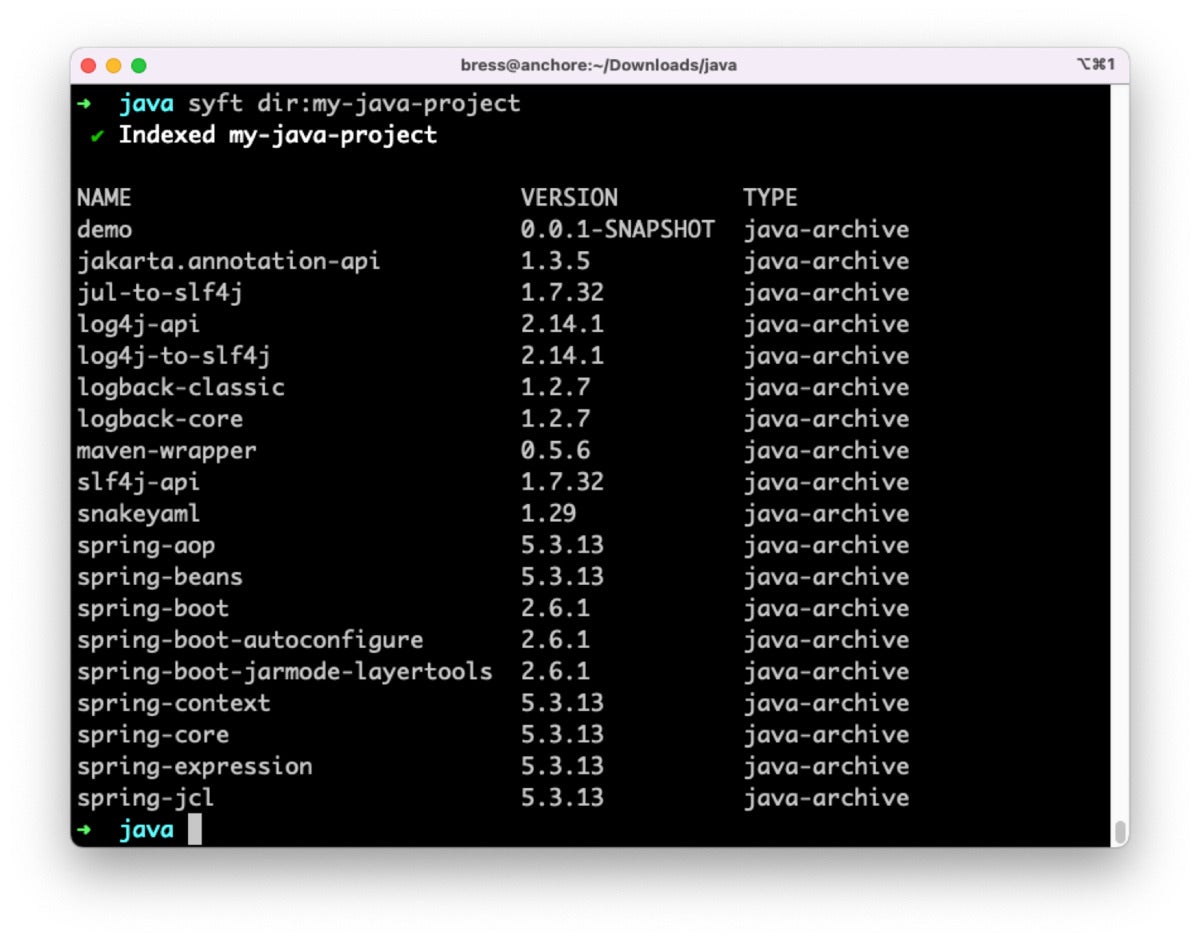
Syft is also ready to discern which variation of Log4j a Java application is made up of. The Log4j JAR can be instantly provided in our undertaking, or it can be hidden absent in a single of the dependencies we include. For example, making use of Syft to scan this sample Java undertaking demonstrates that it involves Log4j variation 2.fourteen.1, which is susceptible to Log4Shell.
No matter of the variation of Log4j that is provided, there is benefit in producing and storing an SBOM to keep a history of all the things that is provided in any program component or application you produce. When a new vulnerability is found, this kind of as Log4Shell, it’s substantially speedier to lookup by way of a repository of SBOMs than it is to come across and scan all of your Java purposes.
Grype is a scanner that has the ability to inform us which distinct vulnerabilities our program is made up of. When you include a dependency in your application you can also establish the vulnerabilities that the dependency is made up of, and so on by way of many amounts of nesting. Grype can scan the program instantly, or scan the SBOM made by Syft. This allows you to re-scan the SBOM for new vulnerabilities even immediately after the program has been deployed or shipped to buyers.
Scanning the exact sample Java undertaking with Grype finds the Log4j vulnerability and identifies it as a significant severity.
 Anchore
AnchoreSyft and Grype have the ability to scan your purposes no subject in which they reside. You can scan a directory on disk, scan a container picture domestically, or even scan a container in a distant registry. You can scan resource code right before making, or the final application immediately after it’s built. It’s vital to scan your purposes throughout each stage of development, just for the reason that a resource code scan is cleanse does not indicate the final establish will be. Even scanning immediately after deployment is a fantastic strategy. Maybe you didn’t pick up a significant Log4j vulnerability past 7 days, but you might this 7 days!
Keep Syft and Grype handy
Any time a new zero-working day vulnerability is learned, it can be challenging and difficult for impacted corporations to remediate the challenge speedily. The initial and most vital stage is to fully grasp if a specific vulnerability even affects you, and in the circumstance of JAR files it can be a problem to fully grasp this without the need of tooling. Anchore’s open resource Grype and Syft tools dig all the way to the base of your dependency tree to establish if there’s a duplicate of Log4j hiding someplace.
As an sector, how we respond and assist each individual other throughout zero-working day vulnerabilities is significant. Now is the time to share remedies and awareness to assistance avoid breaches like this in the coming years.
Josh Bressers is VP of protection at Anchore.
—
New Tech Discussion board presents a venue to take a look at and focus on rising organization technologies in unparalleled depth and breadth. The choice is subjective, based on our pick of the technologies we consider to be vital and of best desire to InfoWorld audience. InfoWorld does not take advertising and marketing collateral for publication and reserves the proper to edit all contributed information. Send all inquiries to [email protected].
This tale, “How to detect the Log4j vulnerability in your purposes” was at first posted by
Macworld Insider.
Copyright © 2021 IDG Communications, Inc.

 Anchore
Anchore





