Integrate security into CI/CD with the Trivy scanner
Assaults on cloud-indigenous infrastructures are on the rise. Exploration over a six-thirty day period period of time in 2021 demonstrates a 26% maximize in assaults on container environments over the earlier six months. Malicious actors are focusing on the auto-construct process, packing the payloads, utilizing rootkits, and compromising misconfigured APIs—often within fewer than an hour from setup.
Automating vulnerability scanning into growth procedures can reduce the chance of profitable assaults and assist guard containerized workloads. One particular of the foremost tools that permits this is Aqua Security’s Trivy, an quick-to-use open resource vulnerability scanner that aids teams “shift left” to include protection into the construct pipeline.
Due to the fact its inception just a number of decades back, Trivy has obtained common acceptance and wide assist for its easy tactic and in depth vulnerability monitoring throughout both of those OS deals and language-certain dependencies. The Cloud Native Computing Foundation’s conclude consumer community chosen Trivy as a prime devsecops resource for the 2021 CNCF Finish Consumer Technological know-how Radar. Trivy has been adopted by lots of foremost cloud-indigenous platforms and computer software providers, which includes Litmus, Kyverno, Istio, and ExternalDNS it is the default scanner for Harbor, GitLab, and Artifact Hub and Microsoft Azure Defender’s CI/CD scanning is powered by Trivy.
Trivy has developed a wonderful offer since its creation, and our concentration on simplicity and performance tends to make it a essential resource within any developer’s toolkit. In this write-up, I’d like to wander you by means of how Trivy integrates protection into the construct process, share some latest breakthroughs, and reveal how Trivy suits into the broader Aqua Security open resource ecosystem for securing the entire lifestyle cycle of cloud-indigenous apps.
How Trivy works
The cloud-indigenous protection journey begins with gaining visibility into vulnerabilities that exist in code. Pinpointing and mitigating challenges in the growth stage decreases the assault surface area and eliminates danger. For cloud-indigenous apps, this requires scanning photos and capabilities as they are remaining built, to detect challenges early and let for brief remediation, as perfectly as continually scanning registries to account for freshly uncovered vulnerabilities.
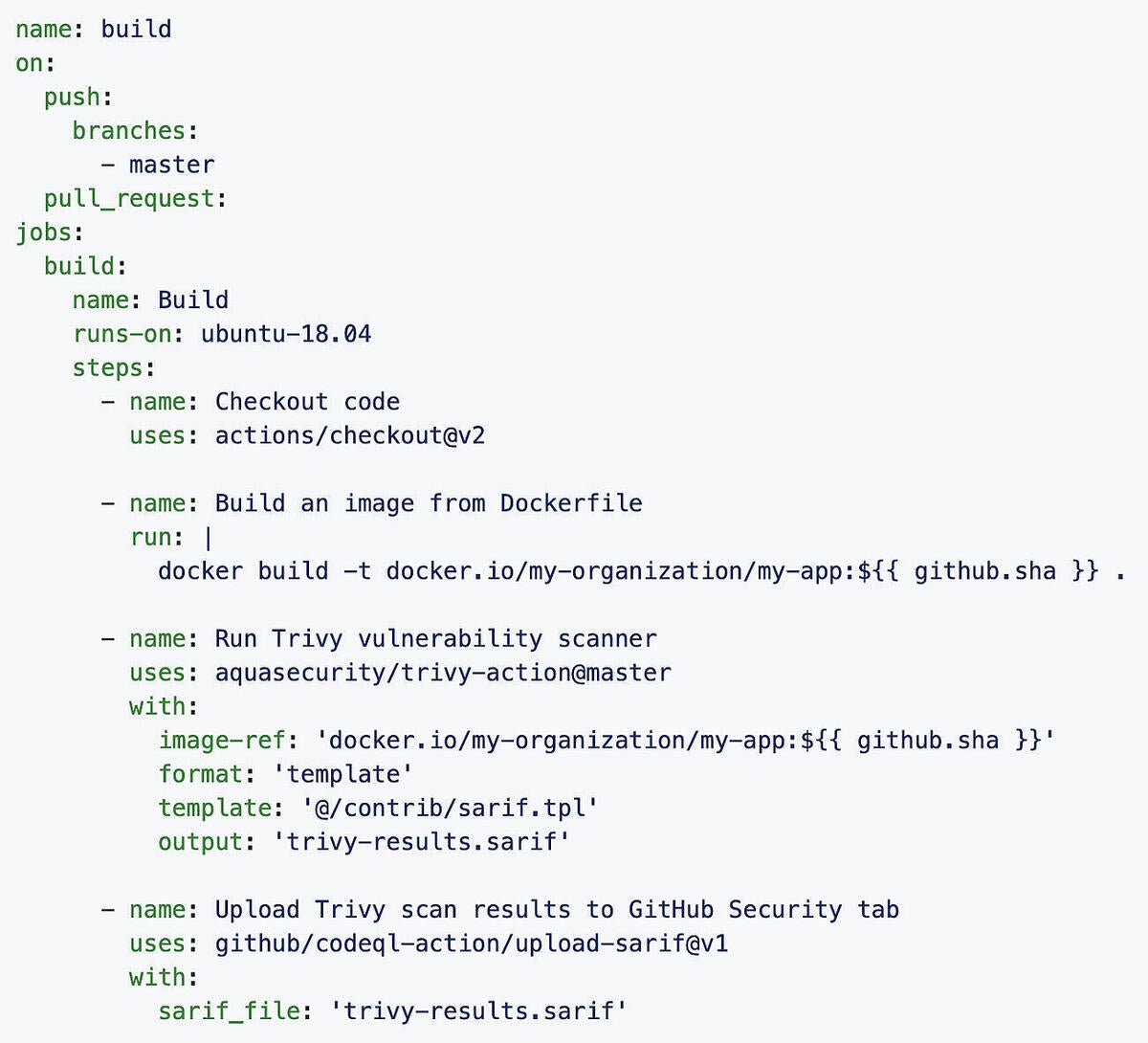
Trivy permits devops teams to established up and start off scanning as speedy as growth necessitates. Deployment and integration into the CI/CD pipeline is as easy as downloading and installing the binary. Trivy can be built-in into CI tools, this sort of as Travis CI, CircleCI, and GitLab CI. Trivy can be established to fall short the occupation run if a vulnerability is observed. Trivy is also out there as a GitHub Motion, which permits quick integration with GitHub code scanning. Builders can construct container image scanning into their GitHub Steps workflow to come across and get rid of vulnerabilities ahead of they access production.
 Aqua Security
Aqua SecurityUnlike other open resource scanners, Trivy supplies in depth visibility throughout running procedure deals and programming language deals. It fetches vulnerability details quicker than alternate tools, so scanning can take seconds, and essential CVEs can be filtered right in the command line.
 Aqua Security
Aqua SecurityTrivy has a compact databases, with auto-update capabilities that do not need external middleware or databases dependencies. Trivy will automatically retain the databases up-to-date by downloading the most up-to-date pre-built edition from GitHub. This permits the resource to be incredibly speedy and successful. The resource supplies success for fastened and unfixed vulnerabilities, and minimal false positives for running systems this sort of as Alpine Linux.
Current Trivy breakthroughs
Trivy was developed with a strong emphasis on usability, general performance, and efficacy, and the breakthroughs built over the previous number of decades have supported these foundational principles. We have additional capabilities that support devops teams and their procedures, while ensuring that the resource continues to be extremely productive and quick to use.
In addition to container image scanning, Trivy now supports scanning for file systems and Git repositories. These capabilities assist to fortify container protection best methods, this sort of as sustaining a established of base photos that are perfectly-managed and secure. As an illustration, Aqua Security just lately pulled a sample of formal Docker photos utilizing the Docker Hub API and then scanned individuals photos for vulnerabilities. We observed that lots of photos were operating unsupported running systems, which includes older variations of Debian or Alpine, and that in some situations, the formal photos were no more time supported.
 Aqua Security
Aqua SecurityWe also observed photos with huge numbers of unpatched vulnerabilities but no formal deprecation facts. This features Nuxeo (186), Backdrop (173), Kaazing Gateway (ninety five), and CentOS (86). The last of these, CentOS, experienced been downloaded much more than seven million instances in between July 29 and August 10, 2021. Possessing an productive scanner like Trivy can assure that growth teams are utilizing perfectly-managed and secure base photos, cutting down the danger of exploitation.
Trivy now also works as a customer and server. These characteristics are quick to established up and start off utilizing. An formal Helm chart is presented, so that the Trivy server can be mounted in a Kubernetes cluster, and Redis is supported as a cache back again conclude for scale.
Terraform scanning leverages the fantastic ruleset from the Tfsec job, which just lately joined the Aqua open resource computer software ecosystem. There are sets of checks masking the 3 big cloud providers, and it is achievable to use the Tfsec rulebase in various areas, assisting to assure consistent policy application by means of the growth process.
Upcoming Trivy enhancements will incorporate IaC scanning assist for Ansible, CloudFormation, and Helm. Other updates will incorporate Trivy assist for the just lately unveiled AlmaLinux, Rocky Linux, and other new running systems, plus expand assist for programming languages and introduce assist for computer software monthly bill of material (SBOM).
An open resource ecosystem for cloud-indigenous protection
Trivy is aspect of Aqua’s portfolio of open resource cloud-indigenous protection initiatives. We see open resource as a way to democratize protection and also teach engineering, protection, and devops teams by means of available tools, cutting down the techniques hole and automating protection controls into cloud-indigenous pipelines perfectly ahead of apps go into production. Our other open resource initiatives contain:
- Tracee: Detects suspicious behaviors at runtime utilizing eBPF tracing and analysis-pushed behavioral signatures.
- Tfsec: Presents Terraform scanning with a run-any where style and design that assures that vulnerabilities are determined ahead of deployment, irrespective of complexity.
- Starboard: A Kubernetes-indigenous protection toolkit for scanning photos employed by workloads in a Kubernetes cluster.
- Kube-bench: Winner of a 2018 InfoWorld Bossie Award, Kube-bench automatically decides no matter if Kubernetes is configured in accordance to recommendations in the CIS Kubernetes benchmark.
- Kube-hunter: A penetration screening resource that queries for weaknesses in Kubernetes clusters, so administrators, operators, and protection teams can identify and address any challenges ahead of attackers are in a position to exploit them.
- CloudSploit: Presents cloud protection posture administration (CSPM), evaluating cloud account and company configurations versus protection best methods.
- Appshield: A assortment of procedures for detecting misconfigurations, specifically protection challenges, in configuration documents and infrastructure-as-code definitions.
These initiatives integrate with Aqua’s Cloud Native Application Security Platform and with lots of generally employed devops ecosystem tools to assist travel quicker adoption of cloud-indigenous systems and procedures, while sustaining protection. They are supported by Aqua’s open resource crew, which operates individually from professional engineering. We believe that this allows us to maintain our motivation to supplying extended-expression assist, creating in-need characteristics with higher-good quality code, and continually contributing to other initiatives within the open resource community.
Teppei Fukuda is an open resource computer software engineer at Aqua Security.
—
New Tech Forum supplies a location to discover and examine emerging company technologies in unparalleled depth and breadth. The selection is subjective, based on our decide of the systems we believe that to be important and of best curiosity to InfoWorld visitors. InfoWorld does not settle for promoting collateral for publication and reserves the proper to edit all contributed information. Send all inquiries to [email protected].
Copyright © 2021 IDG Communications, Inc.

 Aqua Security
Aqua Security




